Introduction
Today we will discuss one important topic of ethical hacking and that is dictionary attack. In this post we will cover below things,
- What is Dictionary Attack.
- Why hackers do this attack.
- Which mechanism or tool is used.
- How to do the dictionary attack (step by step).
Lets see these one by one,
What is dictionary Attack
Dictionary attack is a method of cracking password of any system (OS, Service, network devices, etc.). An attacker uses a list of password (contains a list of commonly used password) and tries each of it with the help of some tools.
Why hackers do this attack
Hackers want to have the control of any systems and for that they need credentials of that system. Most of the cases they try to take control of the Operating System, Web sites and other services (ftp). But sometimes, they want to decrypt the encrypted files (password protected).
Which mechanism or tool is used
Hackers use different tools to crack the password of target system (website, Operating system etc.). One of the most common tool is Hydra by THC. Another tools are also there named Aircrack-ng, Cain & Abel, John the Ripper, Hashcat, DaveGrohl, and ElcomSoft. Most of these tools uses a list of word as a password and list of word an user. With the help of the tool, automatically attempt to login using the list. If any username and password matches, it shows you that.
How to do the dictionary attack (step by step)
Prepare an Attack Machine: To simulate any attack, you need an attack machine. Ethical hackers start learning using Kali linux. You can download the Kali linux ISO and install it in a virtual environment like Hyper-v virtualbox, vmware workstation. Kali has different tools installed by default to practice Ethical Hacking.
Prepare a Target System: To simulate the attack you need a target system. You can install Ubuntu Server Operating System in the same virtual environment.
Create a list of User & Password: You need a list of users and Password for doing the attempt. You can download the the password list from here. Prepare a list of users by your own. Both the list can be saved as .txt
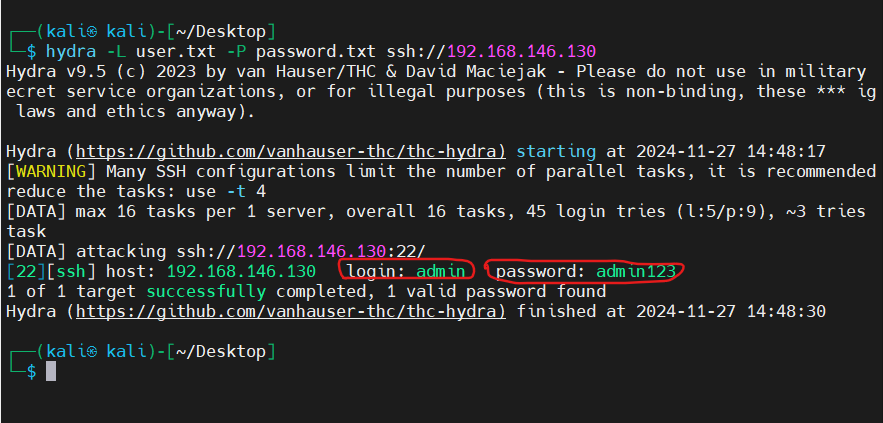
Do the attack: Login to Kali and open a terminal. Run below command to start.
hydra -L user.txt -P password.txt ssh://{ip_address}
Replace ip_address with your target machine IP.
Result: